A New Approach to Prevent the Recurrence of Phishing Domains: Introduction of the "Good Faith Squatting Strategy (Phishing Takeover)"
Tokyo, Japan – August 28, 2024 – ImprovedMove Co. Ltd.. (hereinafter referred to as 'the Company') developed and implemented a new approach called 'Good Faith Squatting Strategy (Phishing Takeover)' on June 20, 2024, aimed at preventing the recurrence of phishing activities. This initiative prevents phishers from re-acquiring domains and protects societal safety.
Following the theoretical foundations of this approach, the Company launched the Good Faith Squatting Service on August 28, 2024. This service specifically targets two aspects to deter phishing fraud: 1) Preventing the reacquisition of phishing domains, and 2) Complicating the operational environment for phishing activities.
Background
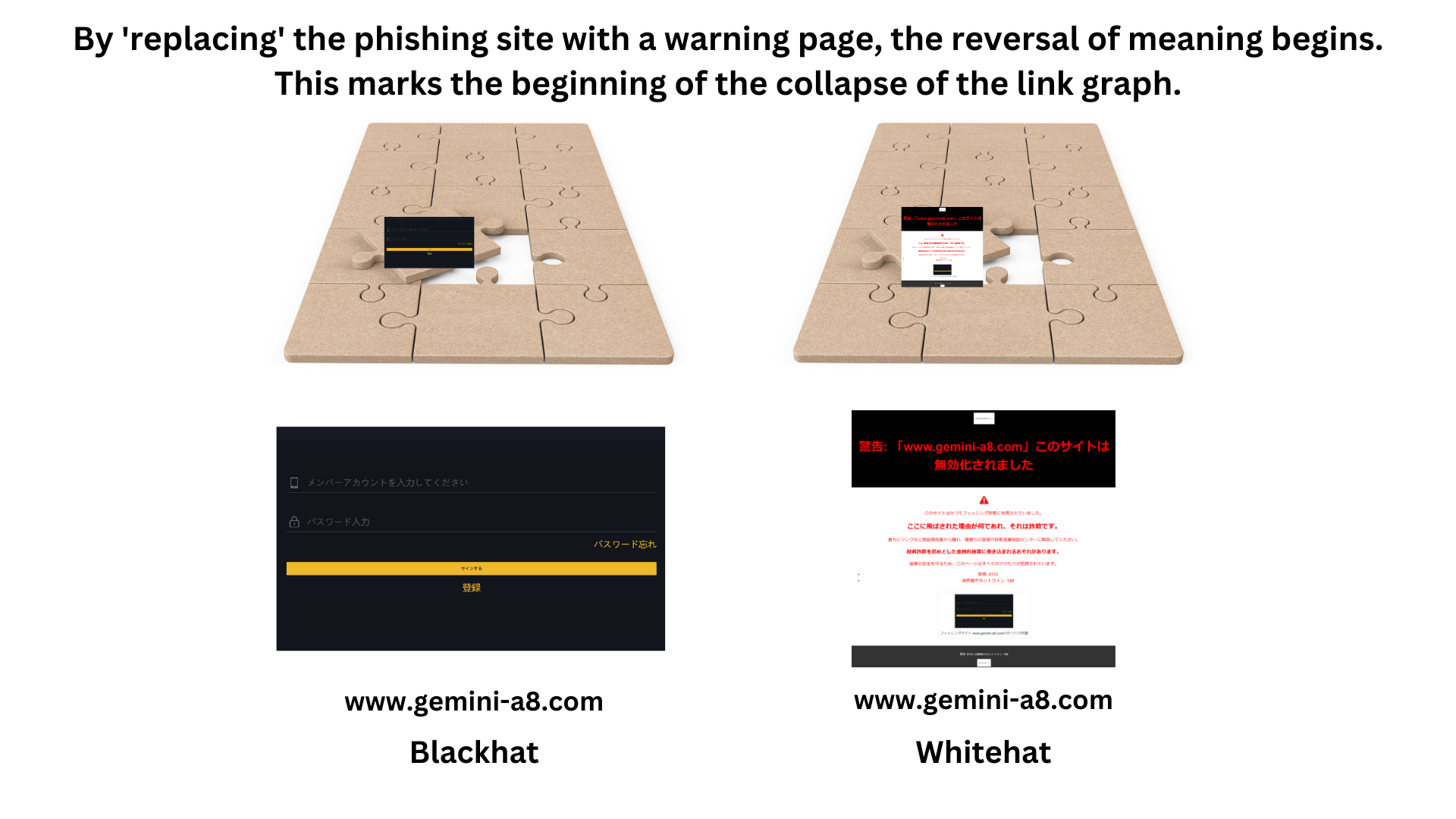
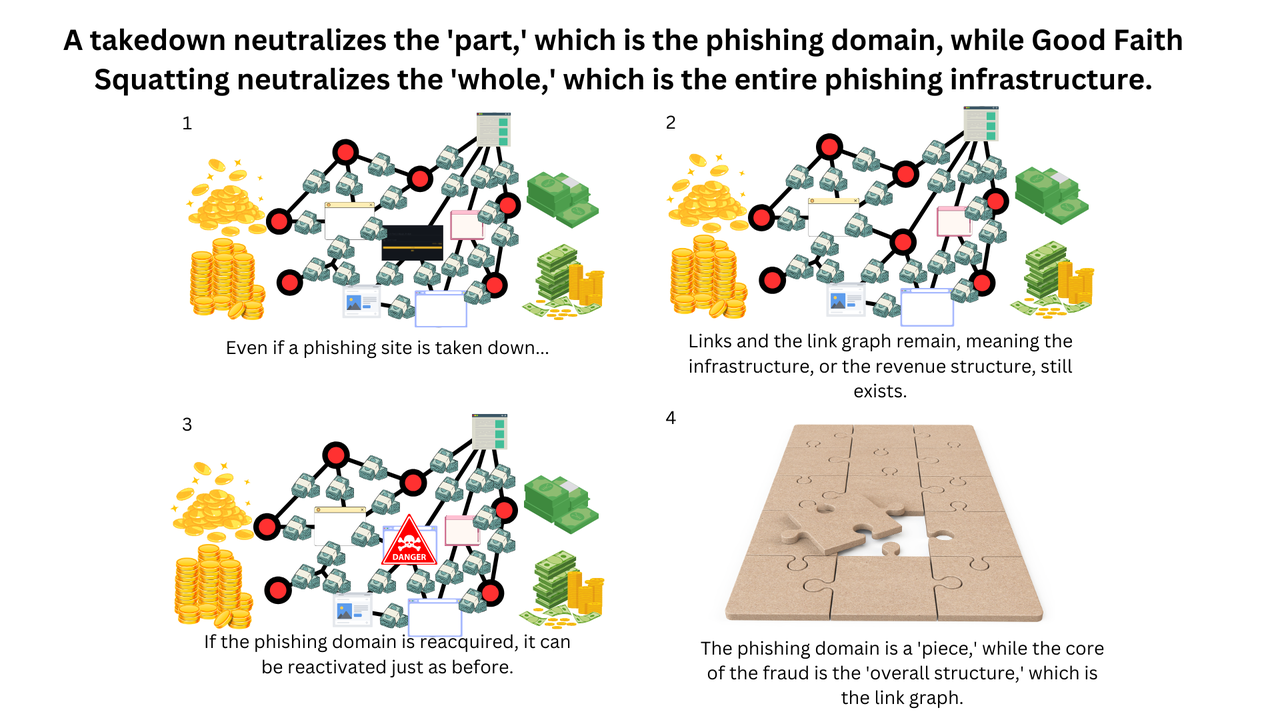
In a phishing site takedown case involving a domestic financial institution with a capital of several billion yen, which our company handled, one of the main threats was the phishing site (www.gemini-a8.com). Although the site was swiftly taken down (deactivated) due to our prompt response, there remained a possibility that phishing actors could reacquire this domain if it was put up for resale.
Even after taking down the phishing site, numerous links to the phishing site remained active. If phishing actors were to reacquire the domain and resume operations, there was a significant risk that potential victims could again fall prey to fraudulent activities.
New Approach
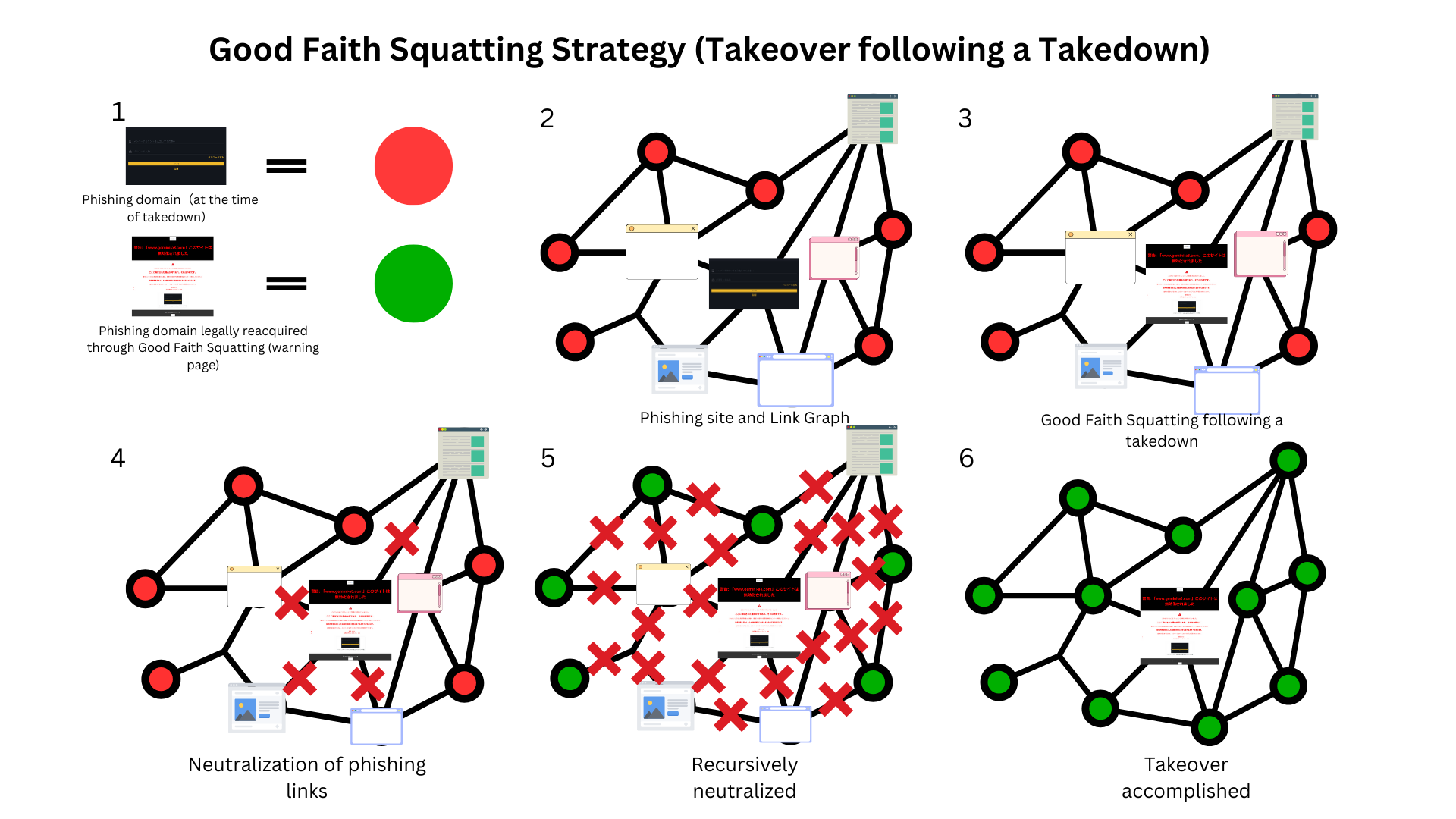
To preemptively mitigate this risk, our company implemented the "Good Faith Squatting Strategy" (Phishing Takeover). This involves our company acquiring ownership of the phishing domain (www.gemini-a8.com) to prevent its reacquisition by phishing actors. Specifically, we acquired the domain immediately after it was put up for sale on the market. This approach also contributes to the preservation and provision of evidence and the prevention of new disguising efforts.
Why It's Necessary to Acquire the Phishing Domain
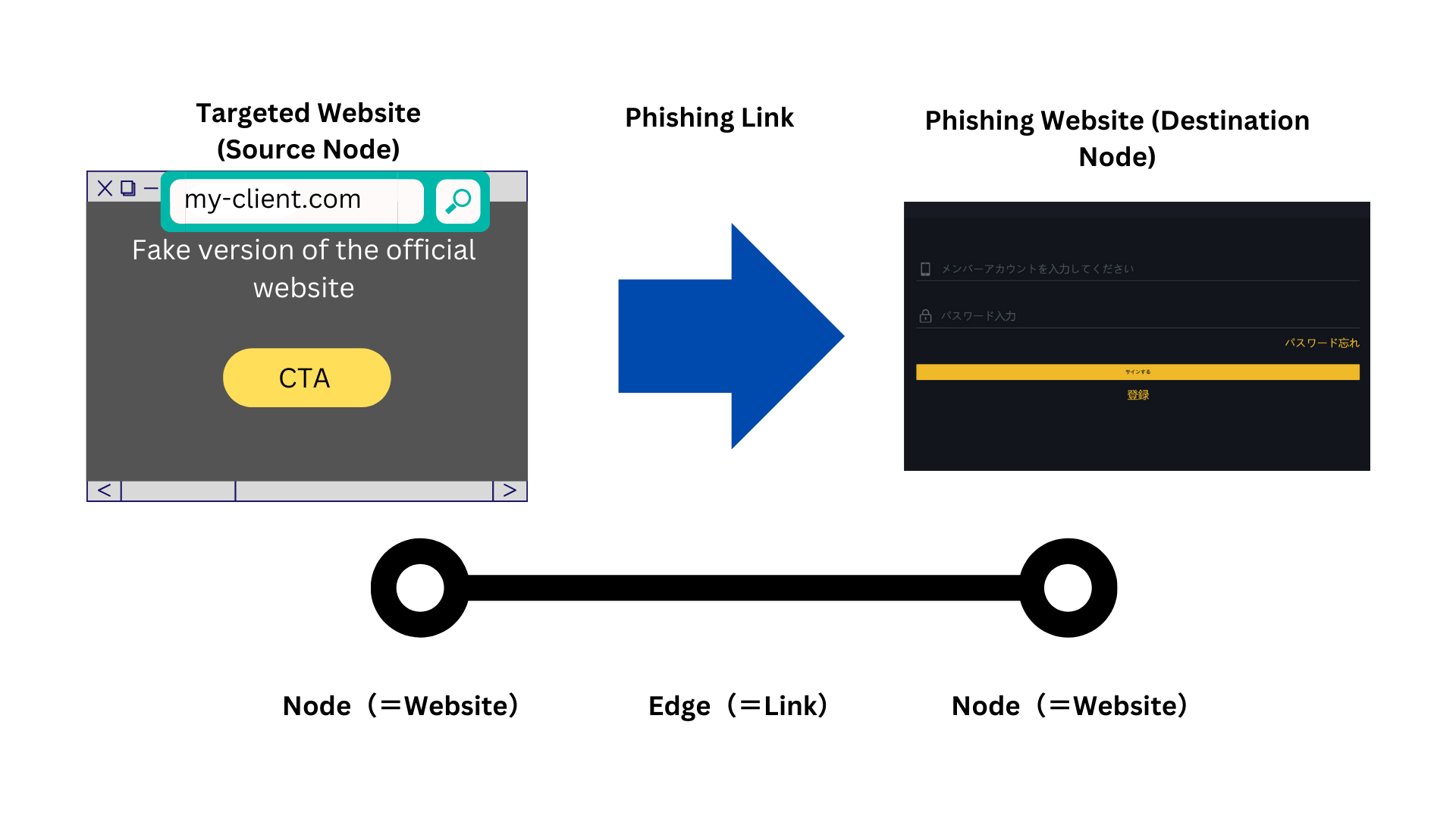
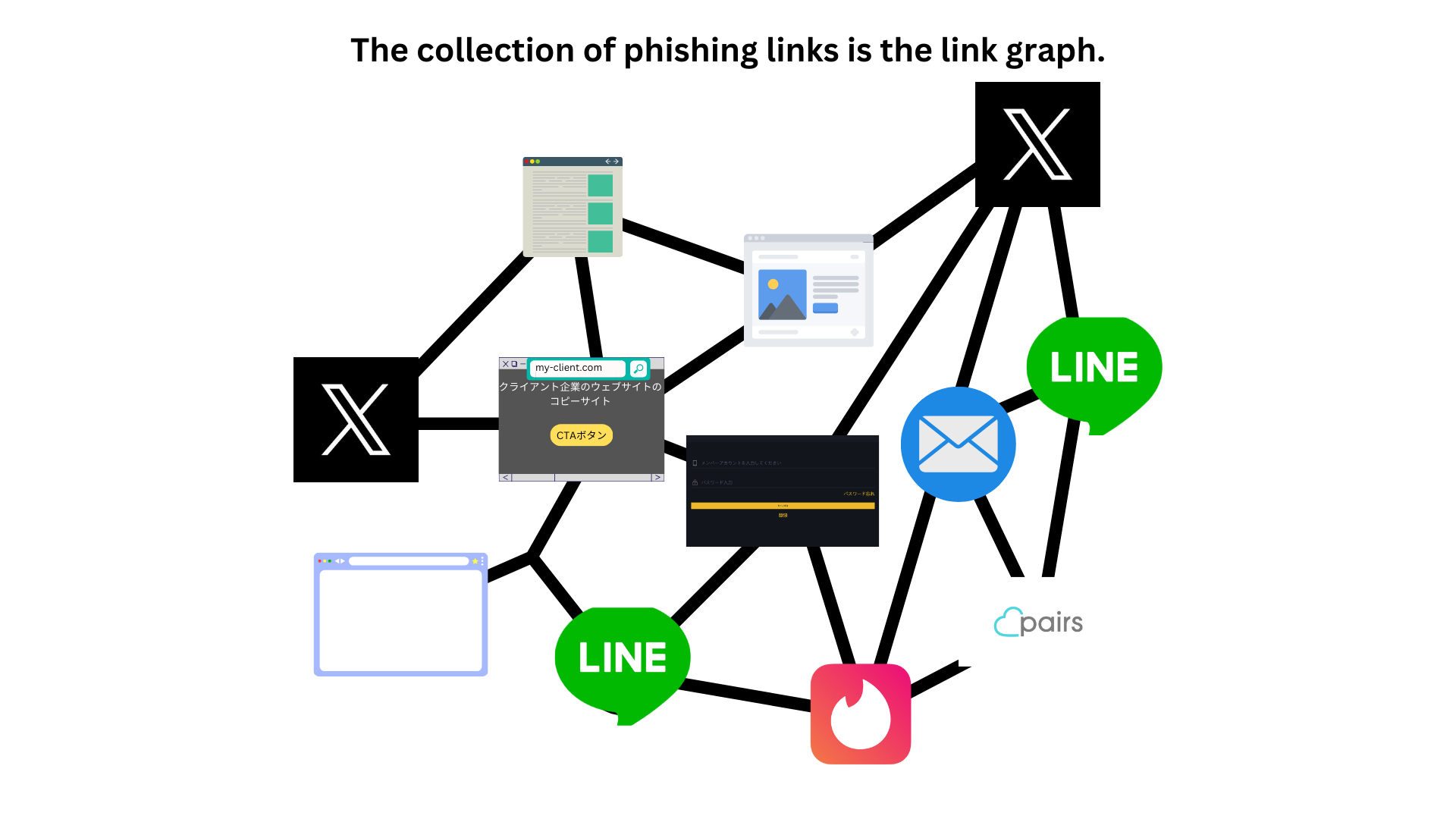
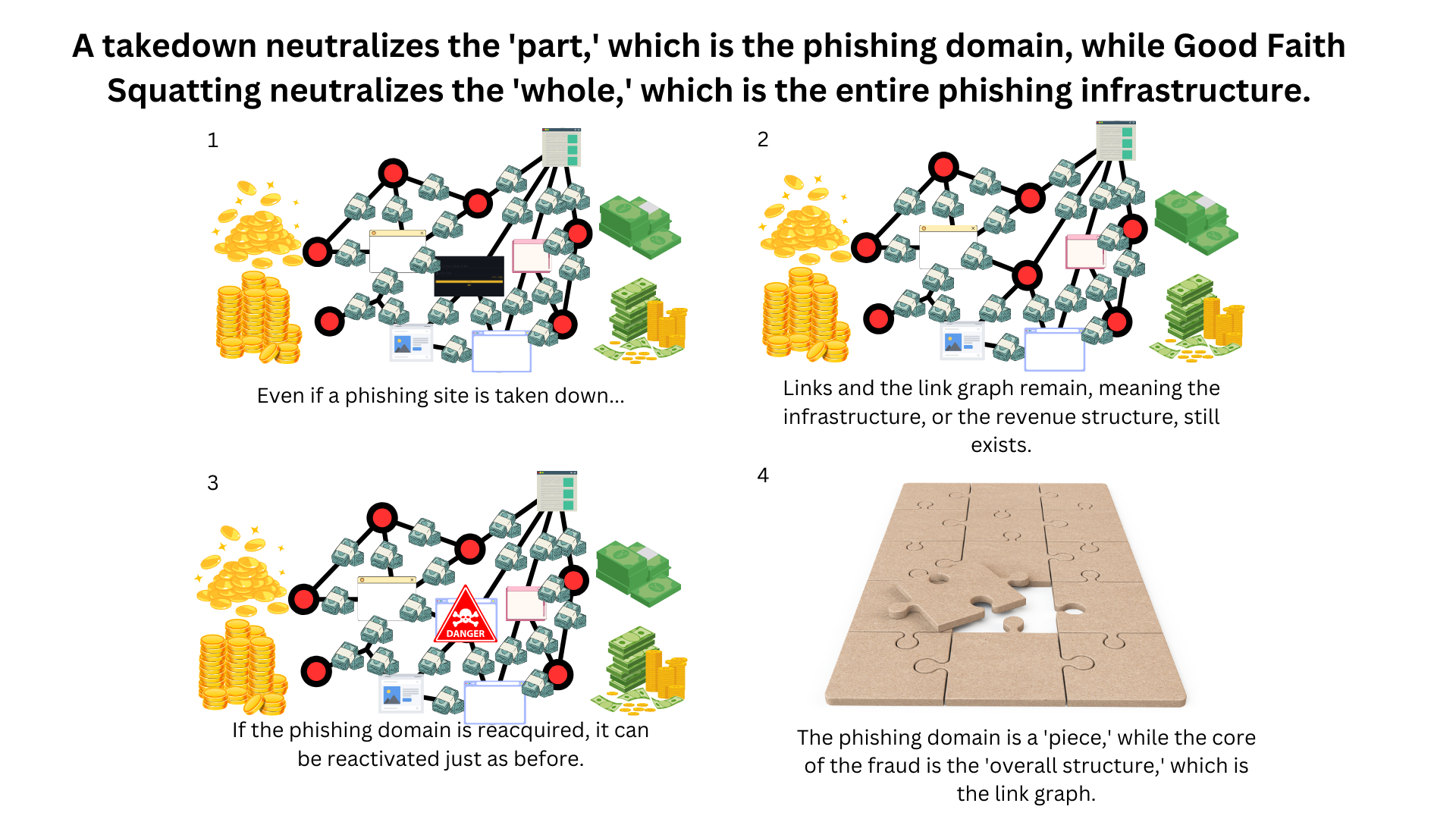
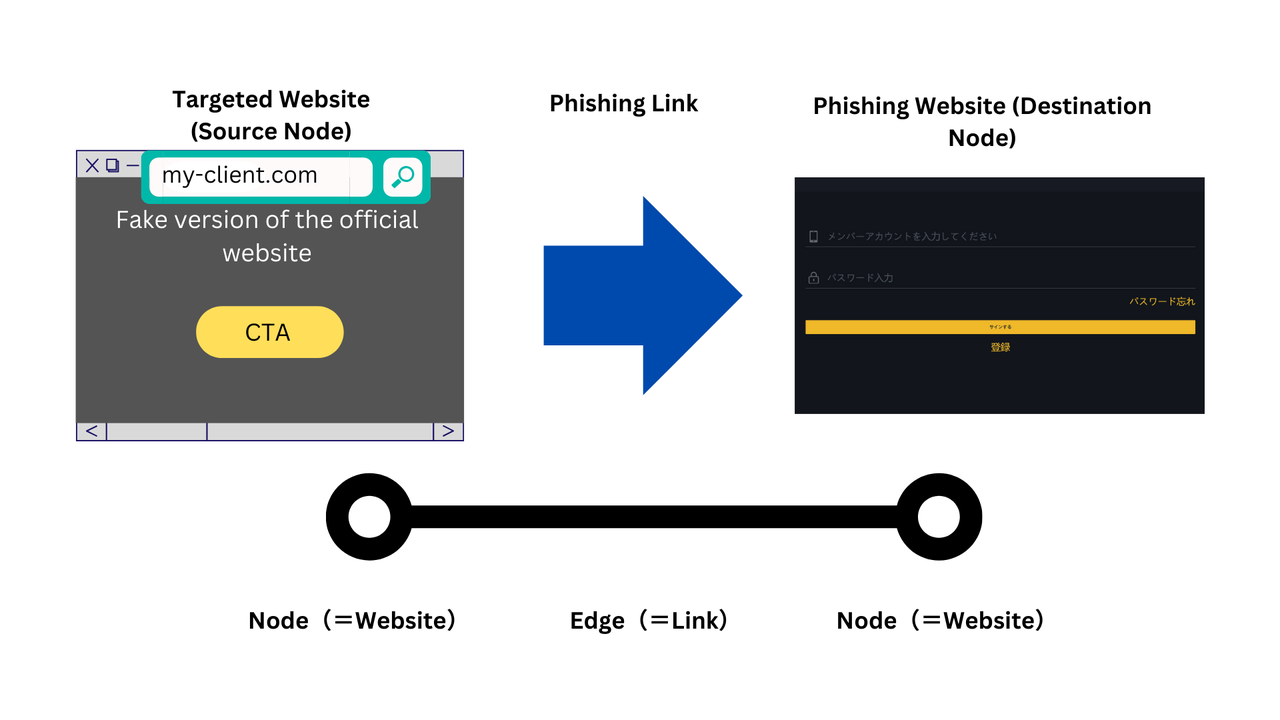
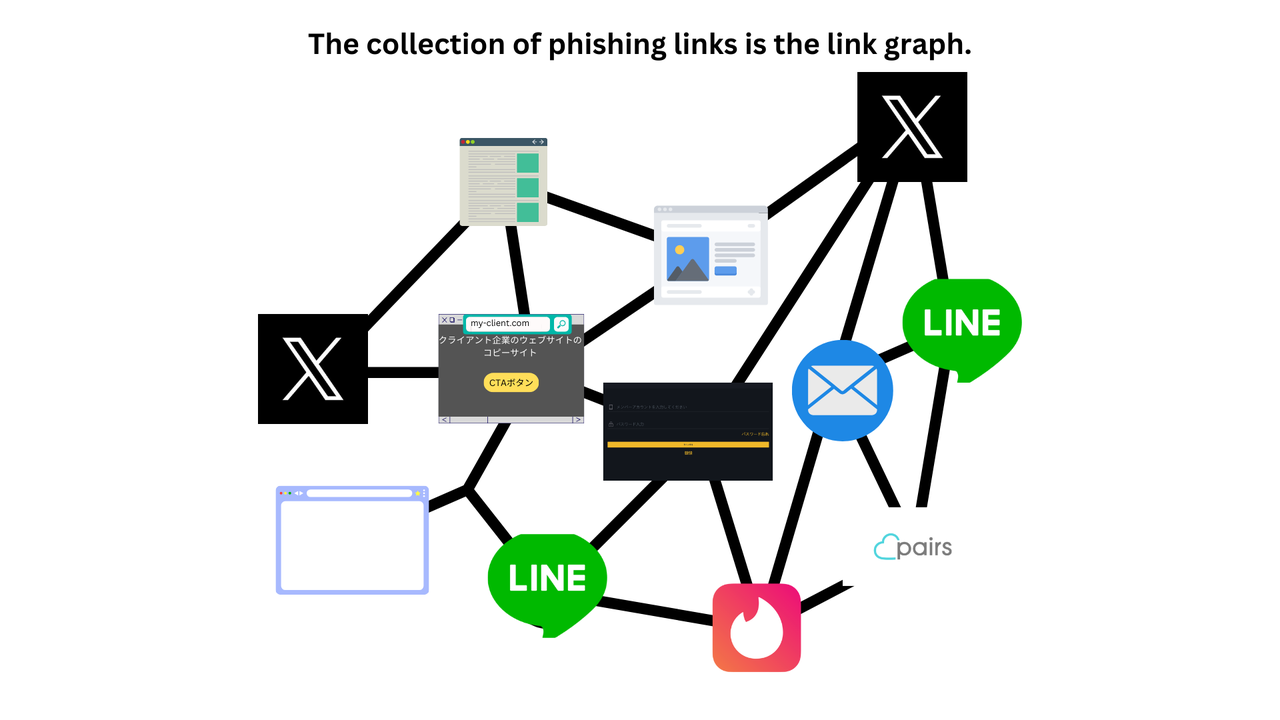
Countless links lead to one destination, making the phishing domain a master key.
Although numerous links exist, they commonly point to a single domain name, which is a significant characteristic of the phishing link graph. Inverting this perspective shows that "controlling the phishing domain name controls the entire link graph." Thus, acquiring the central node (phishing domain) and doing something "contradictory" to the phishers' intentions—such as displaying a warning page and tracking—reverses the arrows and recursively deactivates the entire link graph.
By acquiring the domain and hosting a warning page, we aimed to achieve the following objectives:
Objectives and Effects
- Prevention of Reacquisition by Phishing Actors: By owning the domain, we eliminate the risk of it being reacquired by phishing actors.
- Neutralization of the Entire Link Graph: We neutralize the link graph built by phishing actors, preventing the spread of damage.
- Real-Time Tracking: Tracking through the warning page allows us to uncover the attackers' network and take further countermeasures.
- Raising Awareness Among Potential Victims and Promoting Disconnection from Referring Parties: Through the warning page, we alert potential victims and encourage them to sever ties with phishing actors.
- Collection and Accumulation of Information on Phishing Actors: Tracking enables us to collect information about phishing actors and take countermeasures.
- Preservation of Domain History and Evidence: We maintain the domain's history to provide it as evidence to law enforcement agencies.
- Ensuring Capability to Provide Information to Law Enforcement Agencies: We prepare to provide collected data to law enforcement agencies and collaborate on countermeasures.
- Prevention of New Disguising Efforts: Acquiring the domain prevents phishing actors from engaging in new disguising efforts.
What is a Link Graph?
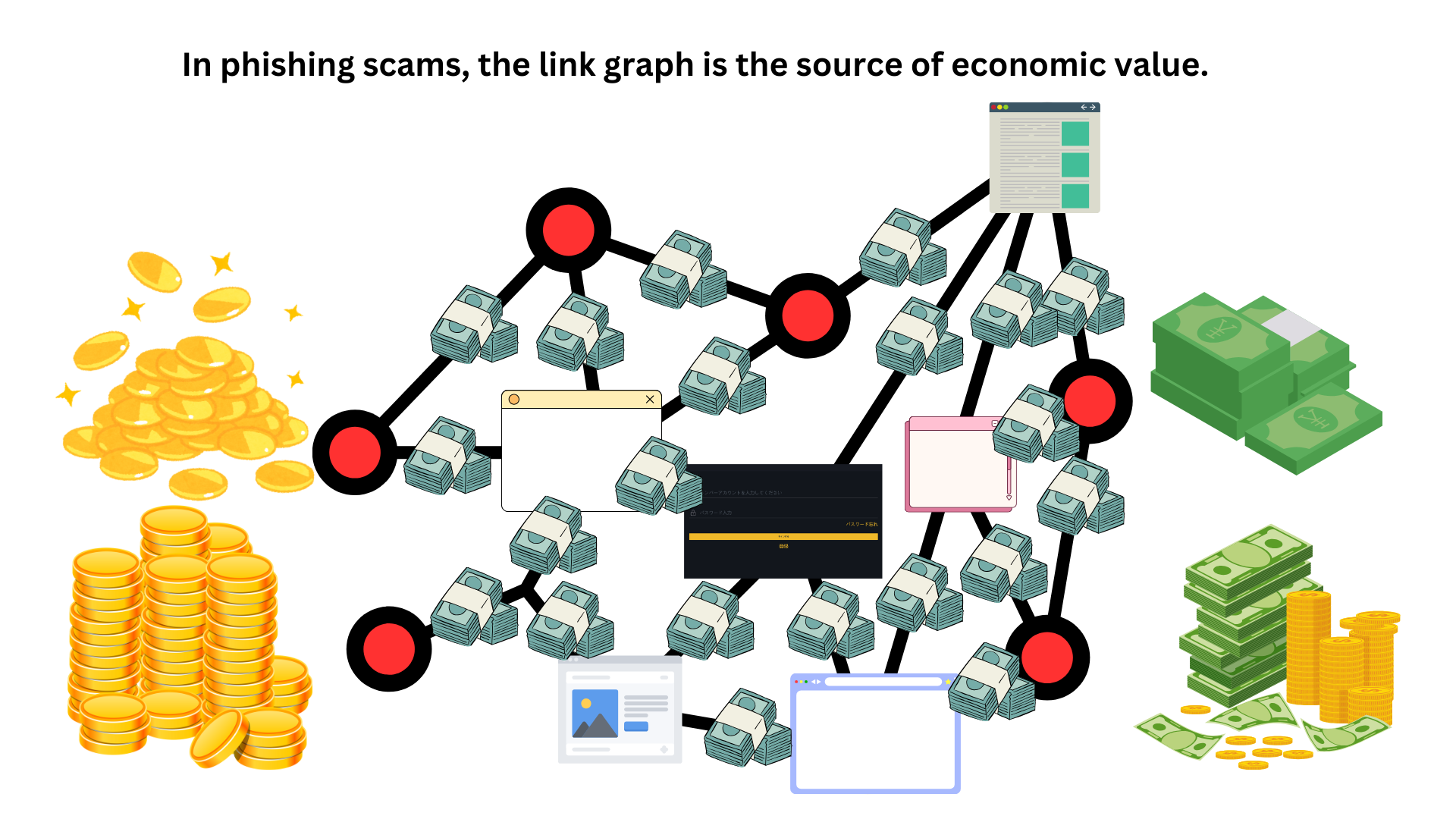
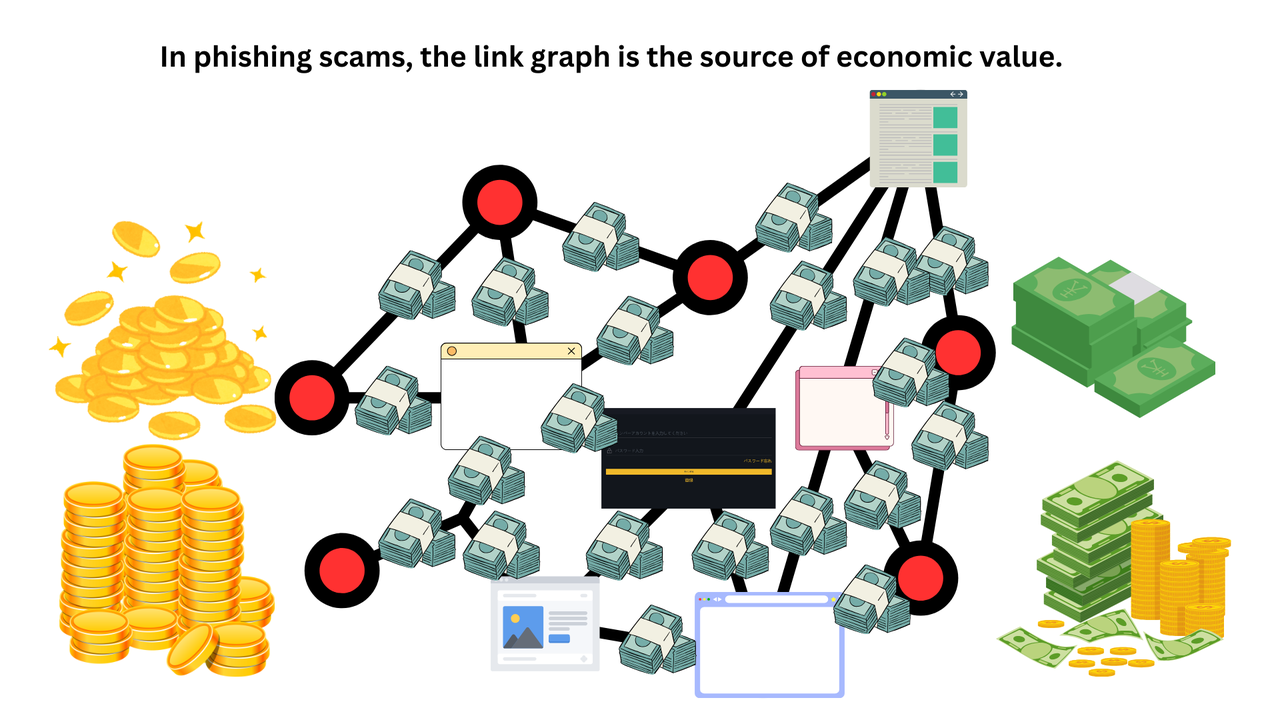
Link Graph as a Source of Economic Value for Phishing Actors
A link graph is a collection of links to phishing sites, playing a crucial role in enhancing the effectiveness of phishing actors' attacks. Each edge (link) can be considered a unit of profit (profit from one victim), and it is viewed as the "core" that creates the market in the phishing fraud business (with phishing sites being the nodes). The loss per unit of phishing fraud can range from tens of millions to billions of yen. The phishing site (www.gemini-a8.com) has been reported to be involved in numerous SNS scams, investment frauds, and cryptocurrency frauds, and was directly involved in phishing fraud against a financial institution client of ours with capital in the billions of yen (for more details on the successful case, please see here).
It can be said that the link graph, rather than the phishing sites (nodes), is the primary source of value for phishing actors.
Reversing the Nature of the Link Graph (From Takedown to Takeover: "Reversing" Risks by Seizing Enemy Infrastructure)
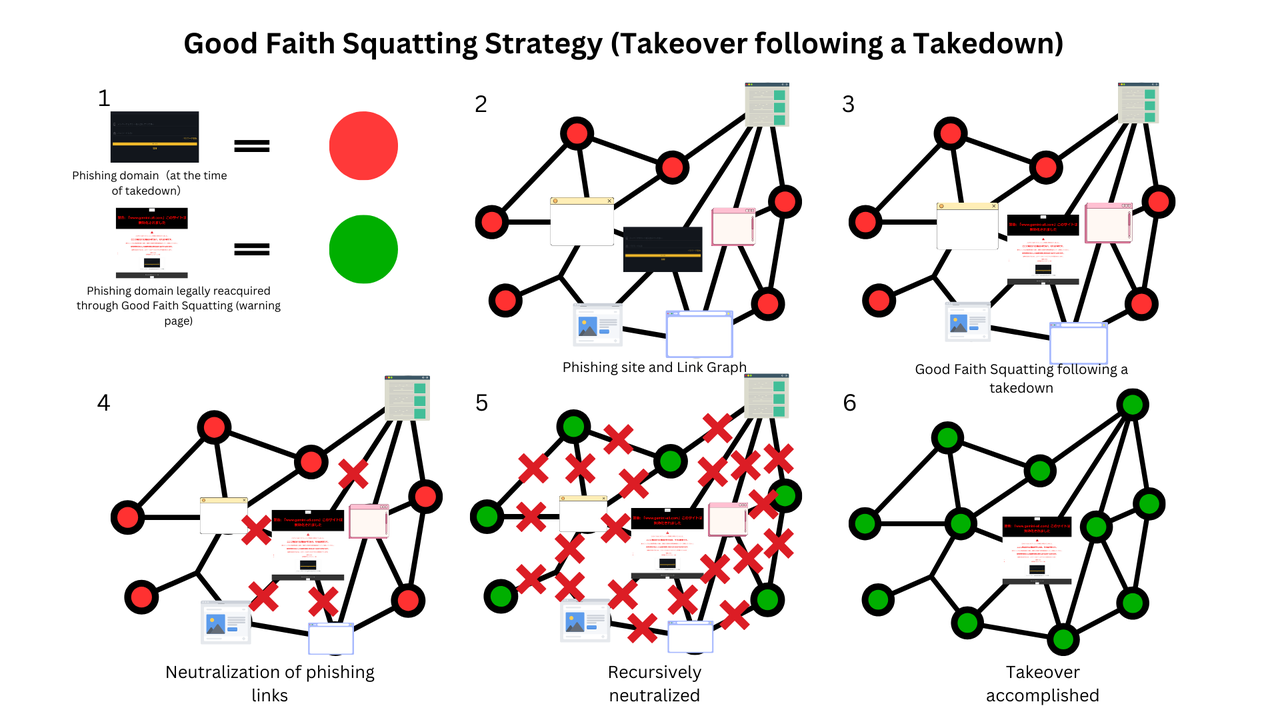
By purchasing the phishing domain after the takedown, hosting a warning page, and conducting tracking there, we invalidate the existing links (this activity is against the interests of phishing actors, and in this case, we host the warning page as an extension of law enforcement, "reversing" the meaning of the links), leading to the neutralization of the entire link graph. In other words, as a countermeasure following a takedown, acquiring the phishing domain, hosting a warning page, and conducting tracking allow us to turn the infrastructure built by phishing actors against them, reversing the direction of the edges and utilizing them for our purposes (from takedown to takeover).
To illustrate this attempt more clearly:
"For example, suppose a fraudster was committing fraud in the city using a fake company name. We would remove the signboard the fraudster used and buy it legally to prevent further fraud at the same location. Then, we would put up a warning saying, 'Fraud was conducted here,' alerting passersby. Moreover, we would stake out the location, watch for the fraudster's return, follow their movements, and eventually locate their base of operations. Meanwhile, we would notify the police to prepare for their arrest in the act. As soon as they arrive, the police would be there to greet them, making the base itself unusable afterward."
In this analogy:
- The takedown corresponds to removing the signboard.
- The legal purchase of the signboard corresponds to acquiring the domain.
- The warning display corresponds to hosting the warning page.
- Tracking corresponds to the stakeout, surveillance, and tailing.
- Evidence preservation corresponds to collaboration with law enforcement agencies.
- The link graph corresponds to the base of operations.
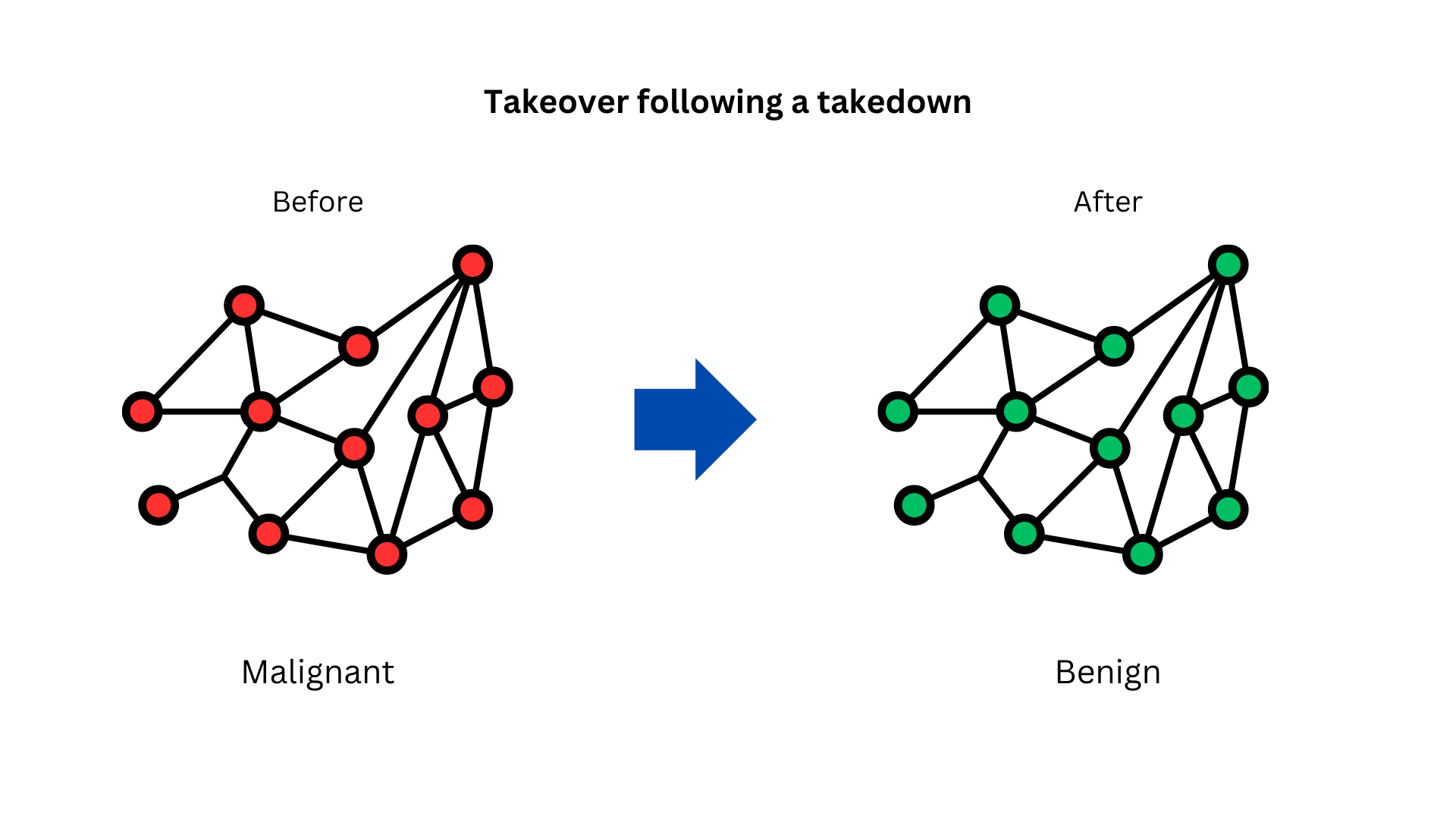
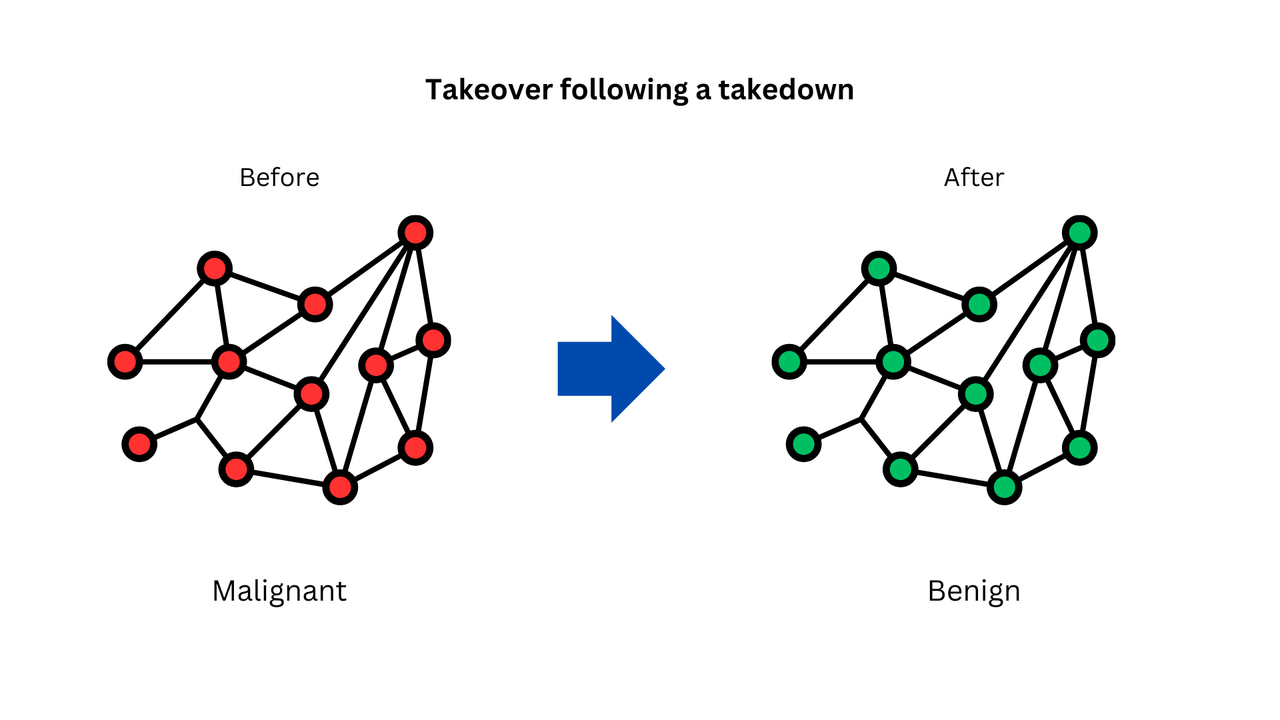
This approach of acquiring a phishing domain and hosting a warning page with tracking allows us to 'reverse' the entire link graph (base of operations) built by phishing actors through their fraudulent links. In other words, by seizing the central node (phishing domain) and changing its status, this change propagates recursively (BFS/DFS), transforming the entire graph's state (from malicious to benign), much like flipping pieces in the game of Othello. Indeed, this is a takeover following a takedown. Phishing actors find themselves trapped by the link graph they created.
The invalidation of links occurs naturally due to the presence of the warning page, causing the entire link graph to collapse without any further human intervention. This is a noteworthy point: it is a necessary result of the node's meaning being reversed from malicious to benign. The collapse of the link graph is expected to progress in a step-by-step fashion, similar to BFS or DFS.


Possible Objection
One possible objection to good faith squatting is that it can collapse the entire link graph, but what if phishers shorten the cycle of domain acquisition and abandonment, shifting to a style of fraud that this approach cannot counter? Here's how we can respond:
The length of the cycle and the size of the link graph (number of links) are proportional. Shortening the cycle reduces the size of the link graph due to the time and cost required for construction. When the link graph is smaller, its influence and economic impact also decrease, forcing phishers to face a trade-off. To increase effectiveness, they need to expand the graph size, but this also increases the damage caused by good faith squatting. Avoiding this requires them to keep the graph size small and the cycle short, which lowers the economic effect. Structurally, this forces a reconsideration of their approach, maintaining the effectiveness of our strategy.
In other words, opportunities for monetization that existed post-takedown through reacquisition are now limited to a smaller timeframe from acquisition to abandonment (takedown), effectively reducing the economic impact due to the 'shortening of the time frame.'
Launch of Good Faith Squatting Service
Based on these analyses, ImprovedMove Co. Ltd.. began offering the Good Faith Squatting Service on August 28, 2024. This service aims to prevent the recurrence of phishing domains in two specific ways: 1) Preventing the reacquisition of phishing domains, and 2) Creating an environment that makes it difficult to continue phishing scams by neutralizing the phishing link graph.
Conclusion
Since June 20, 2024, ImprovedMove Co. Ltd.. has acquired and become the owner of the phishing domain (www.gemini-a8.com). As previously mentioned, the purpose of this acquisition is to prevent the expansion of scams using this domain and to achieve the deactivation of the underlying phishing infrastructure (link graph).
Based on this theoretical background, ImprovedMove Co. Ltd.. began offering the Good Faith Squatting Service on August 28, 2024. This service focuses on preventing the recurrence of phishing fraud from two aspects: 1) Preventing the reacquisition of phishing domains, and 2) Making the operational environment for phishing fraud more difficult.
Our efforts are legally and ethically justified and play an important role in preventing the recurrence of phishing activities. We will continue to make our best efforts to ensure the safety of society.
Disclaimer
Please be aware that our company acquired the phishing domain (www.gemini-a8.com) on June 20, 2024, and we had no prior involvement with this domain before this date. Also, rest assured that the acquisition process was conducted legally, following the standard purchasing process through an authorized domain seller after the phishing domain was listed for sale on the market. All compliance measures have been met in this regard.
Receive the Latest Security Updates Now
By filling out the form, you'll receive timely updates on the latest services to help strengthen your company's security.