Website Vulnerabilities: How to Disable Directory Listing and Why It’s Crucial for Security
June 2, 2023
When directory listing is enabled, unintended files may become publicly accessible, increasing the risk of information leaks. In Nginx, directory listing is controlled by the autoindex directive, which can sometimes be unintentionally enabled. This guide explains how to check if directory listing is enabled, why it’s a security risk, and how to disable it in Nginx. Protect your website with this essential security practice.
How to Check if Directory Listing is Enabled
There are primarily three methods to verify if directory listing is enabled on your website. The first is accessing via a URL pattern, the second uses the Curl command, and the third involves vulnerability scanning tools. Below, we'll explore each method.
Checking via URL Pattern
To verify if directory listing is enabled via URL, follow these steps:
- Access your website through a browser.
- Append a slash (
/) at the end of your URL, e.g., http://example.com/. - If a directory page appears, directory listing is enabled, showing a list of files and directories.
- If no page appears, directory listing is disabled.
Checking Using Curl Command
Use the following Curl command:
curl -s -o /dev/null -I -w "%{http_code}" http://example.com/Replace http://example.com/ with your website URL. If directory listing is enabled, it will return an HTTP status code "200". If disabled, you'll see "403" (Forbidden) or "404" (Not Found).
Another method involves using vulnerability scanning tools to verify directory listing status.
Security Risks of Directory Listing
If directory listing is enabled, the files and directories on your website may be publicly accessible, presenting several security risks:
- Exposure of Sensitive Information: Files that should remain confidential may be inadvertently exposed, leaking sensitive data externally.
- Website Structure Exposure: Attackers can easily understand your website’s structure, making it easier to target specific vulnerabilities or critical files.
- Ease of Navigation for Attackers: Attackers can easily traverse the file system, potentially accessing files outside the root directory, compromising important or confidential information.
- Enhanced Attack Planning: Attackers gain insights into your internal website structure and available files, enabling more targeted and effective attacks.
Keeping directory listing enabled significantly elevates these risks. Therefore, disabling directory listing is crucial for strengthening your website’s security and preventing unintended information leakage.

Example
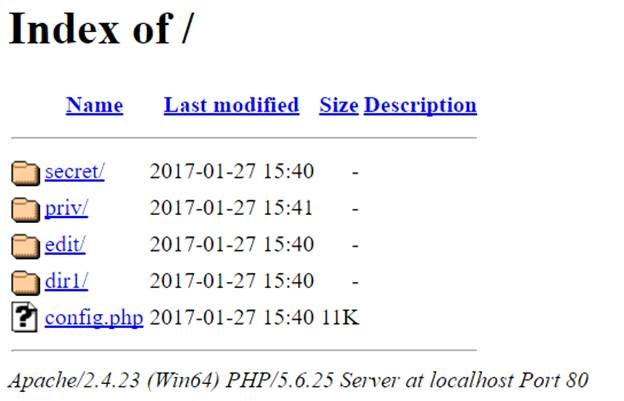
If directory listing is enabled, files and folders on your server might become accessible as shown below:
In the illustrated example, even folders like "Secret," which should not be publicly accessible, become easily viewable by anyone through direct URLs.
If using a CMS, non-public folders or files could become externally accessible. Sensitive files managed through the administration panel might inadvertently become publicly viewable.
Thus, enabling directory listing substantially increases information leakage risks.
How to Disable Directory Listing in Nginx
Below is how to disable directory listing in Nginx:
Open the /etc/nginx/nginx.conf file, locate the location / directive within the server block, and add autoindex off;. If autoindex on; is already present, simply change it to autoindex off;.
Before Change:
server {
listen 80;
server_name domain.com www.domain.com;
location / {
autoindex on; # Change this
}
}After Change:
server {
listen 80;
server_name domain.com www.domain.com;
location / {
autoindex off; # Changed
}
}This prevents external users from browsing directory contents.
After updating, verify by accessing your domain again with the trailing /. If the directory listing no longer appears, the configuration change was successful, and your website’s non-public information is now secured from external viewing.