Website Vulnerabilities: Missing Subresource Integrity (SRI) and Its Security Risks
May 31, 2023
Without Subresource Integrity (SRI), your website is at risk of executing malicious code if external resources are tampered with. This can compromise user security, damage trust in your site, and expose sensitive data. Learn why SRI is crucial and how to implement it to protect your website and users.
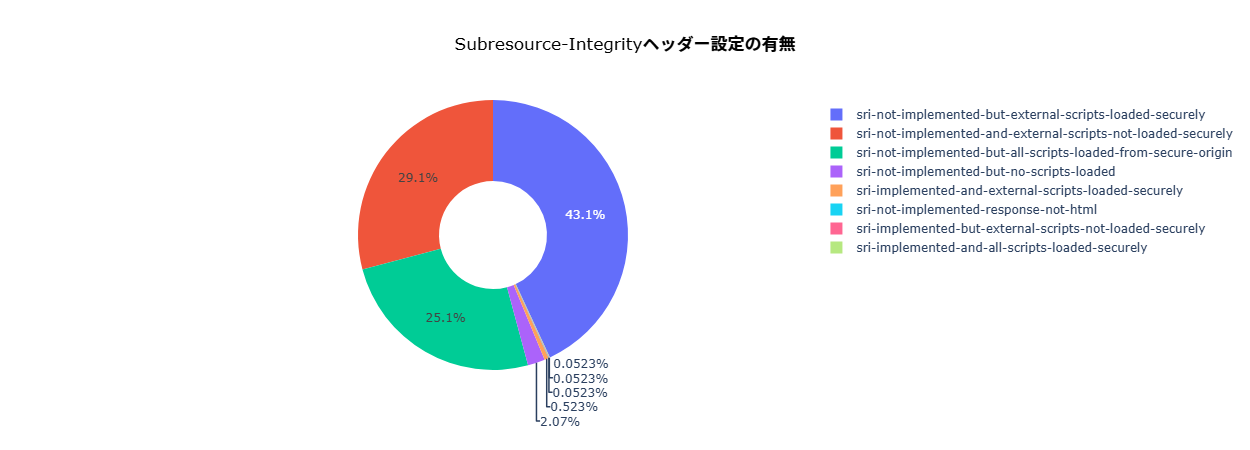
Problems of Not Setting Subresource Integrity (SRI)
If Subresource Integrity (SRI) is not set, the following issues may arise:
1. Source Tampering
If SRI is not configured, external sources (such as scripts and stylesheets) may be maliciously modified. Attackers can alter resources over the network, and if a compromised resource is loaded into a user’s browser, untrusted code or malware may be executed.
2. Reduced Source Reliability
Without SRI, resources that are supposed to be provided by trusted sources may have been tampered with by third parties. This reduces the reliability of the source and increases the risk of exposing user data to security threats.
3. Decreased Cache Efficiency
Without SRI, browsers cannot fully utilize resource caching. Each time the resource content changes, the browser must download a new version. This increases page load time and may degrade performance.
SRI is an effective security measure to prevent resource tampering. It uses a hash value to verify the integrity of the resource, ensuring that only trusted resources are used. By implementing SRI, the risk of attacks and data breaches can be reduced.
How to Set Up Subresource Integrity (SRI)
To configure SRI, you need to add the integrity and crossorigin attributes to the <script> and <link> elements in HTML. Below are examples of how to do this:
Example of Setting SRI in a <script> Element
<script src="example.js" integrity="sha256-xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx" crossorigin="anonymous"></script>- The
srcattribute specifies the JavaScript file to be loaded. - The
integrityattribute contains the resource’s hash value to verify its integrity. - The
crossorigin="anonymous"attribute ensures proper cross-origin request handling.
Example of Setting SRI in a <link> Element (CSS File)
<link rel="stylesheet" href="styles.css" integrity="sha256-xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx" crossorigin="anonymous">- The
hrefattribute specifies the CSS file. - The
integrityattribute contains the hash value for verification. - The
crossorigin="anonymous"attribute is required for correct cross-origin handling.
To obtain the correct SRI hash, you need to compute the hash of the actual file using a hashing function (e.g., SHA-256). Tools and web services are available for generating these hash values.
Important Notes
- If the resource is updated or changed, you must recalculate and update the hash value.
- While SRI helps protect against resource tampering, it is not a complete security solution. It should be used alongside other security measures.
Using an SRI Hash Generator
SRI Hash Generator is a free online tool that helps generate the required hash values. Follow these steps to generate an SRI hash:
- Prepare the file you want to generate a hash for (e.g.,
example.js). - Visit an SRI Hash Generator website, such as:
- Enter or upload the file content.
- Select the SHA-256 algorithm.
- Click the generate button to get the hash value.
- Copy the generated hash and set it in the
integrityattribute.
Example Using an SRI Hash Generator
<script src="example.js" integrity="sha256-V5YS8+JmUocYcThfMT/2jFkh9SRNn8FQ8g7PRt7d/Xo=" crossorigin="anonymous"></script>This ensures the file is loaded only if it matches the specified hash.
Cyberattacks That Can Occur Without SRI
Failing to implement SRI can lead to various cyber threats:
1. Resource Tampering
Without SRI, attackers can modify external resources such as scripts and stylesheets. If the browser loads a tampered resource, malicious code or malware may be executed.
2. File Substitution
Without SRI, attackers can use the same URL to serve a different, malicious file. By replacing the original resource with a compromised one, attackers can execute malicious scripts or inject harmful code.
3. Cross-Site Scripting (XSS)
Without SRI, attackers can use external scripts to perform XSS (Cross-Site Scripting) attacks. If an attacker injects a tampered script, it may run in the user’s browser, leading to session hijacking and data leakage.
SRI ensures the browser verifies the integrity of resources using hash values. By enabling SRI, websites can protect against resource tampering and cyberattacks.