BEAST Vulnerability and Countermeasures
July 31, 2023
What is the BEAST Vulnerability?
BEAST (Browser Exploit Against SSL/TLS) is a vulnerability in certain versions of the SSL/TLS protocol that was publicly disclosed in 2011. It primarily affects versions of TLS 1.0 and earlier, as well as some implementations of SSL 3.0.
BEAST is associated with an attack method targeting block ciphers, specifically an attack on the Cipher Block Chaining (CBC) mode used in some block cipher encryption schemes.
Attackers can act as intermediaries on a network, intercepting or tampering with communication between clients and servers. This allows them to extract sensitive data such as encrypted HTTP cookies.
To mitigate the BEAST vulnerability, it is recommended to avoid using vulnerable protocol versions such as TLS 1.0 and earlier, and instead use newer versions like TLS 1.1 or above. In certain environments, using encryption algorithms that do not rely on CBC mode, such as RC4, is also recommended.
The Risks of the BEAST Vulnerability
When the BEAST vulnerability was first discovered, its impact was considered highly severe. The ability to intercept or tamper with communication between clients and servers through a man-in-the-middle attack posed a significant risk to the security of personal and confidential information.
One of the most critical concerns was the potential for attackers to steal user authentication credentials, such as session IDs stored in HTTP cookies, which could allow attackers to impersonate users and access web services.
However, most modern web browsers have since addressed this issue and now default to using newer TLS versions. Likewise, server-side measures have been implemented, significantly reducing the likelihood of a successful attack exploiting this vulnerability.
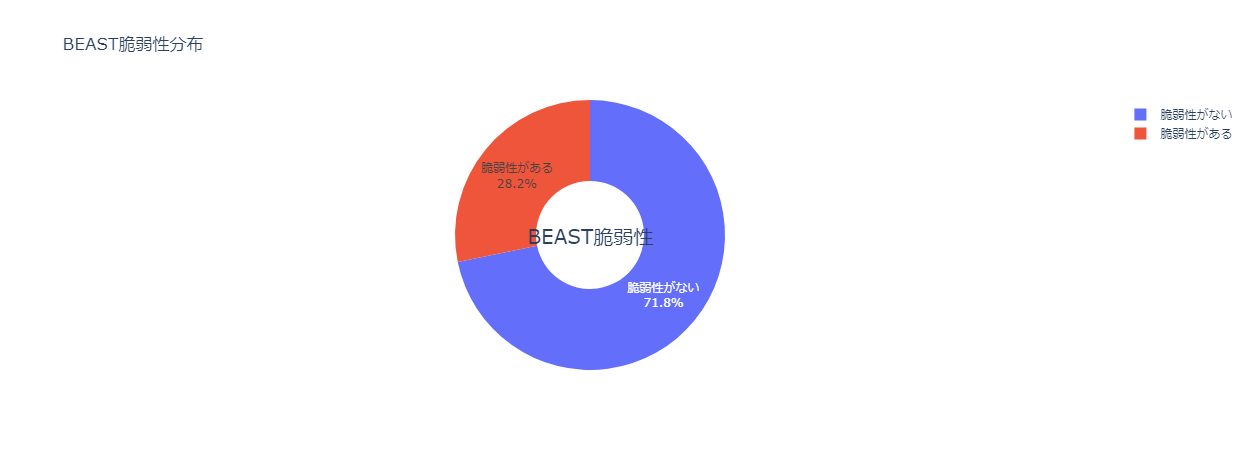
That said, if your website is still vulnerable to the BEAST attack, it indicates that your site is using outdated SSL/TLS protocol versions or has improper server configurations. While this may theoretically expose your site to man-in-the-middle attacks and information leakage, in reality, the chances of such an attack are quite low.
Nevertheless, to ensure the highest level of security, it is advisable to address the BEAST vulnerability. This involves reviewing your server configurations and, if necessary, updating them to ensure that the latest and most secure TLS versions are in use.
How to Address the BEAST Vulnerability
As of now, TLS 1.3 is considered the latest and most secure protocol. TLS 1.3 resolves many vulnerabilities present in earlier versions, including the BEAST vulnerability. Moreover, it incorporates newly developed security features that greatly enhance overall safety.
On the other hand, older protocols such as TLS 1.0 and 1.1 are fraught with vulnerabilities, making them exploitable by attackers. Therefore, it is crucial to avoid using these outdated protocols.
While most modern browsers automatically use the latest and most secure protocols, if a server only supports older protocols, even the latest browsers will communicate using those outdated versions. To prevent this, it is essential to ensure that server configurations support newer protocols.
Solutions for the BEAST Vulnerability
The specific solution for addressing the BEAST vulnerability is to discontinue the use of protocols below TLS 1.1 on your web server. It is necessary to exclude SSL 2.0, SSL 3.0, TLS 1.0, and TLS 1.1 from the protocol settings.
The most direct solution is to exclude protocols below TLS 1.2, as shown below:
ssl_protocols TLSv1.2 TLSv1.3;For Apache, the configuration would look like this:
SSLProtocol all -SSLv2 -SSLv3 -TLSv1 -TLSv1.1Preventing the BEAST vulnerability requires modern configurations at the server software level, which is both essential and effective. Mozilla offers an SSL Configuration Generator, which can generate templates for modern settings. Using this tool is recommended for consistency and ease of implementation.
A modern configuration would look like this:
# generated 2023-10-23, Mozilla Guideline v5.7, nginx 1.17.7, OpenSSL 1.1.1k, modern configuration
# https://ssl-config.mozilla.org/#server=nginx&version=1.17.7&config=modern&openssl=1.1.1k&guideline=5.7
server {
listen 80 default_server;
listen [::]:80 default_server;
location / {
return 301 https://$host$request_uri;
}
}
server {
listen 443 ssl http2;
listen [::]:443 ssl http2;
ssl_certificate /path/to/signed_cert_plus_intermediates;
ssl_certificate_key /path/to/private_key;
ssl_session_timeout 1d;
ssl_session_cache shared:MozSSL:10m; # about 40000 sessions
ssl_session_tickets off;
# modern configuration
ssl_protocols TLSv1.3;
ssl_prefer_server_ciphers off;
# HSTS (ngx_http_headers_module is required) (63072000 seconds)
add_header Strict-Transport-Security "max-age=63072000" always;
# OCSP stapling
ssl_stapling on;
ssl_stapling_verify on;
# verify chain of trust of OCSP response using Root CA and Intermediate certs
ssl_trusted_certificate /path/to/root_CA_cert_plus_intermediates;
# replace with the IP address of your resolver
resolver 127.0.0.1;
}Apache
# generated 2023-10-23, Mozilla Guideline v5.7, Apache 2.4.41, OpenSSL 1.1.1k, modern configuration
# https://ssl-config.mozilla.org/#server=apache&version=2.4.41&config=modern&openssl=1.1.1k&guideline=5.7
# this configuration requires mod_ssl, mod_socache_shmcb, mod_rewrite, and mod_headers
<VirtualHost *:80>
RewriteEngine On
RewriteCond %{REQUEST_URI} !^/\.well\-known/acme\-challenge/
RewriteRule ^(.*)$ https://%{HTTP_HOST}$1 [R=301,L]
</VirtualHost>
<VirtualHost *:443>
SSLEngine on
SSLCertificateFile /path/to/signed_cert_and_intermediate_certs
SSLCertificateKeyFile /path/to/private_key
# enable HTTP/2, if available
Protocols h2 http/1.1
# HTTP Strict Transport Security (mod_headers is required) (63072000 seconds)
Header always set Strict-Transport-Security "max-age=63072000"
</VirtualHost>
# modern configuration
SSLProtocol all -SSLv3 -TLSv1 -TLSv1.1 -TLSv1.2
SSLHonorCipherOrder off
SSLSessionTickets off
SSLUseStapling On
SSLStaplingCache "shmcb:logs/ssl_stapling(32768)"