Complete Guide to TLS 1.3 Configuration for Nginx and Apache: Minimizing Security Risks
March 15, 2024
The quickest way to configure TLS 1.3 is by adding "TLSv1.3" to the ssl_protocols directive in the configuration files of web server software like Nginx or Apache. Below is a detailed step-by-step explanation.
How to Configure TLS 1.3
Enabling TLS 1.3 in Nginx
- Install OpenSSL 1.1.1 or later: To use TLS 1.3, you need OpenSSL 1.1.1 or higher. If your system is using an older version, upgrade to the latest one.
- Update Nginx Configuration: Edit the Nginx configuration file (typically found at
/etc/nginx/nginx.confor within site-specific configuration files) to enable TLS 1.3 by including thessl_protocolsdirective.
server {
listen 443 ssl;
ssl_protocols TLSv1.2 TLSv1.3; # Enable TLS 1.2 and TLS 1.3
ssl_ciphers [appropriate cipher suite];
...
}Restart Nginx: Apply the changes by restarting Nginx.
sudo systemctl restart nginxEnabling TLS 1.3 in Apache
- Install OpenSSL 1.1.1 or later: Similar to Nginx, you need OpenSSL 1.1.1 or above.
- Update Apache Configuration: Edit the Apache configuration file (typically
/etc/httpd/conf/httpd.confor site-specific files) and use theSSLProtocoldirective to enable TLS 1.3.
<VirtualHost *:443>
SSLEngine on
SSLProtocol -all +TLSv1.2 +TLSv1.3
SSLCipherSuite [appropriate cipher suite]
...
</VirtualHost>Restart Apache: Apply the changes by restarting Apache.
sudo systemctl restart httpdRemoving Older Protocols
In addition to adding TLSv1.3 to the SSLProtocols directive, it is important to disable older protocols like SSL v3, TLS 1.0, and TLS 1.1. This can be achieved by excluding protocols below TLSv1.2 in the configuration. This applies to both Nginx and Apache.
TLS 1.3 Support in Web Browsers
Most modern web browsers support TLS 1.3 by default. While no special configuration is typically needed, you can check whether your browser supports TLS 1.3 or whether a specific site is using it by reviewing browser settings or developer tools.
Automatically Generate TLS 1.3-Compatible Configuration Files: Mozilla SSL Configuration Generator
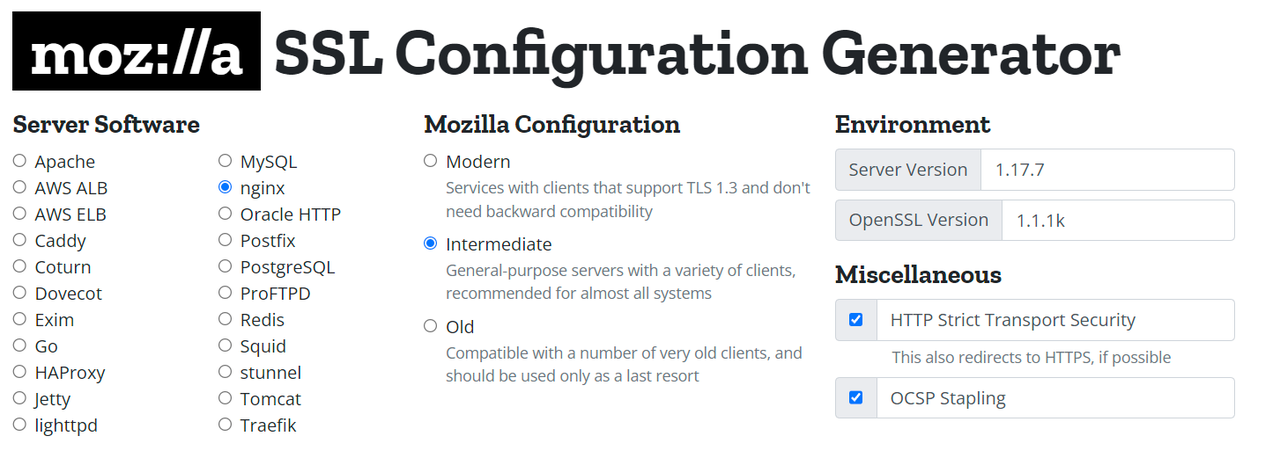
You can easily generate server configuration templates compatible with TLS 1.3 using the Mozilla SSL Configuration Generator. By selecting the relevant server software and choosing either "Modern" or "Intermediate" from the Mozilla Configuration options, you can generate an optimized configuration. Below is an example of an intermediate configuration generated for Nginx.
Mozilla SSL Configuration Generator TLS 1.3-Compatible Code for Nginx (Intermediate Configuration)
# generated 2024-03-11, Mozilla Guideline v5.7, nginx 1.17.7, OpenSSL 1.1.1k, intermediate configuration
# https://ssl-config.mozilla.org/#server=nginx&version=1.17.7&config=intermediate&openssl=1.1.1k&guideline=5.7
server {
listen 80 default_server;
listen [::]:80 default_server;
location / {
return 301 https://$host$request_uri;
}
}
server {
listen 443 ssl http2;
listen [::]:443 ssl http2;
ssl_certificate /path/to/signed_cert_plus_intermediates;
ssl_certificate_key /path/to/private_key;
ssl_session_timeout 1d;
ssl_session_cache shared:MozSSL:10m; # about 40000 sessions
ssl_session_tickets off;
# curl https://ssl-config.mozilla.org/ffdhe2048.txt > /path/to/dhparam
ssl_dhparam /path/to/dhparam;
# intermediate configuration
ssl_protocols TLSv1.2 TLSv1.3;
ssl_ciphers ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-CHACHA20-POLY1305;
ssl_prefer_server_ciphers off;
# HSTS (ngx_http_headers_module is required) (63072000 seconds)
add_header Strict-Transport-Security "max-age=63072000" always;
# OCSP stapling
ssl_stapling on;
ssl_stapling_verify on;
# verify chain of trust of OCSP response using Root CA and Intermediate certs
ssl_trusted_certificate /path/to/root_CA_cert_plus_intermediates;
# replace with the IP address of your resolver
resolver 127.0.0.1;
}Mozilla SSL Configuration Generator TLS 1.3-Compatible Code for Apache (Intermediate Configuration)
# generated 2024-03-11, Mozilla Guideline v5.7, Apache 2.4.41, OpenSSL 1.1.1k, intermediate configuration
# https://ssl-config.mozilla.org/#server=apache&version=2.4.41&config=intermediate&openssl=1.1.1k&guideline=5.7
# this configuration requires mod_ssl, mod_socache_shmcb, mod_rewrite, and mod_headers
<VirtualHost *:80>
RewriteEngine On
RewriteCond %{REQUEST_URI} !^/\.well\-known/acme\-challenge/
RewriteRule ^(.*)$ https://%{HTTP_HOST}$1 [R=301,L]
</VirtualHost>
<VirtualHost *:443>
SSLEngine on
# curl https://ssl-config.mozilla.org/ffdhe2048.txt >> /path/to/signed_cert_and_intermediate_certs_and_dhparams
SSLCertificateFile /path/to/signed_cert_and_intermediate_certs_and_dhparams
SSLCertificateKeyFile /path/to/private_key
# enable HTTP/2, if available
Protocols h2 http/1.1
# HTTP Strict Transport Security (mod_headers is required) (63072000 seconds)
Header always set Strict-Transport-Security "max-age=63072000"
</VirtualHost>
# intermediate configuration
SSLProtocol all -SSLv3 -TLSv1 -TLSv1.1
SSLCipherSuite ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-CHACHA20-POLY1305
SSLHonorCipherOrder off
SSLSessionTickets off
SSLUseStapling On
SSLStaplingCache "shmcb:logs/ssl_stapling(32768)"What is TLS 1.3?
TLS 1.3 refers to version 1.3 of the Transport Layer Security (TLS) protocol, used to securely transmit data over the internet. TLS is widely employed for secure data exchange in activities such as website browsing, email communication, instant messaging, and Voice over IP (VoIP).
Released in 2018, TLS 1.3 offers several critical improvements over previous versions:
- Faster Connections: TLS 1.3 simplifies the handshake process during connection establishment, enabling faster and more secure connections by reducing round-trip time.
- Enhanced Security: Older and insecure encryption methods and protocol features are removed, focusing on safer encryption methods. This improves resistance to attacks, such as man-in-the-middle threats.
- Forward Security: TLS 1.3 enforces forward secrecy, ensuring that even if session keys are compromised, past communications remain secure.
- Improved Privacy: Session resumption mechanisms have been optimized, allowing faster re-establishment of secure sessions while enhancing privacy.
Given its ability to significantly improve both the security and efficiency of internet communications, TLS 1.3 is increasingly adopted by websites and online services.
Why TLS 1.3 is Necessary
TLS 1.3 is critical for improving security, performance, and privacy. Here are some key advantages over older versions:
- Enhanced Security:
- Removal of Vulnerable Features: Insecure cipher suites and functions from earlier versions have been eliminated, reducing the risk of exploitation.
- Mandatory Forward Security: All connections in TLS 1.3 use forward security, meaning that even if encryption keys are exposed in the future, past communications remain protected.
- Improved Performance:
- Simplified Handshake Process: TLS 1.3 reduces the round-trips needed for connection establishment, improving communication speed, especially in high-latency networks.
- Optimized Session Resumption: Resumed sessions use stored information to quickly and securely establish connections.
- Privacy Protection:
- Encrypted Handshake: TLS 1.3 encrypts communication from the earliest stage of the handshake, making it more difficult for intermediaries to observe the details of the connection.
- Compatibility and Future-Proofing:
- Widespread Support: TLS 1.3 is supported by major browsers and operating systems, providing up-to-date security for users and systems.
- Future Security Standards: As threats evolve, TLS 1.3 is built to meet the latest security requirements and provide a foundation for future improvements.
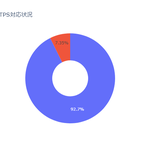
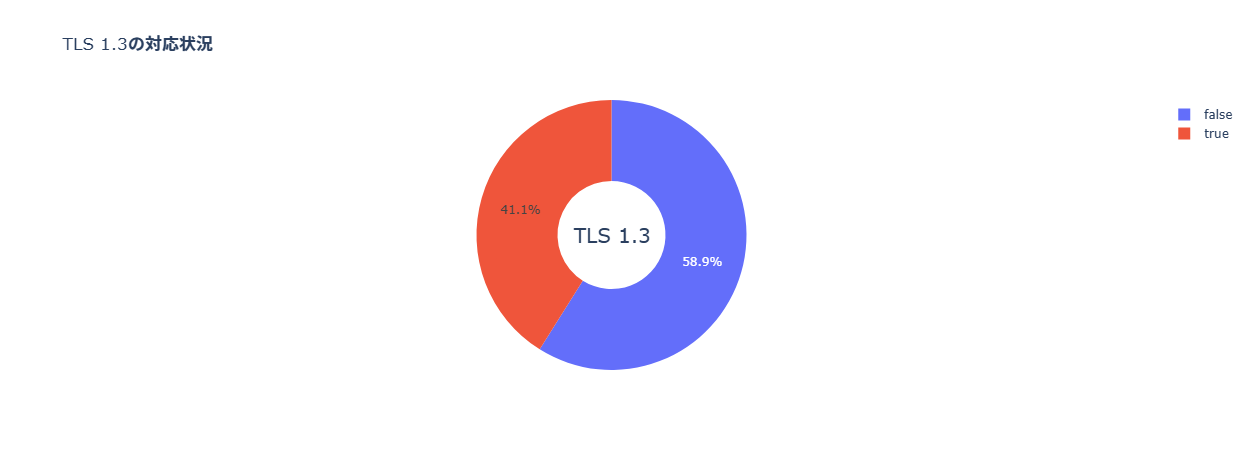
TLS 1.3 Compliance Rate for Japanese Listed Companies: 44.1%
A survey conducted on the TLS 1.3 adoption rate for 3,715 official websites of Japanese listed companies shows that, as of July 2023, the overall compliance rate for TLS 1.3 in Japan is 41.1%.

The TLS 1.3 adoption rates across different industries in Japan are as follows (with the has_tls13 metric representing TLS 1.3 adoption rates). The highest rate is 64% in the airline industry, while the lowest is 15% in the pulp and paper industry. In the latter, only 15% of companies in the industry have adopted TLS 1.3.
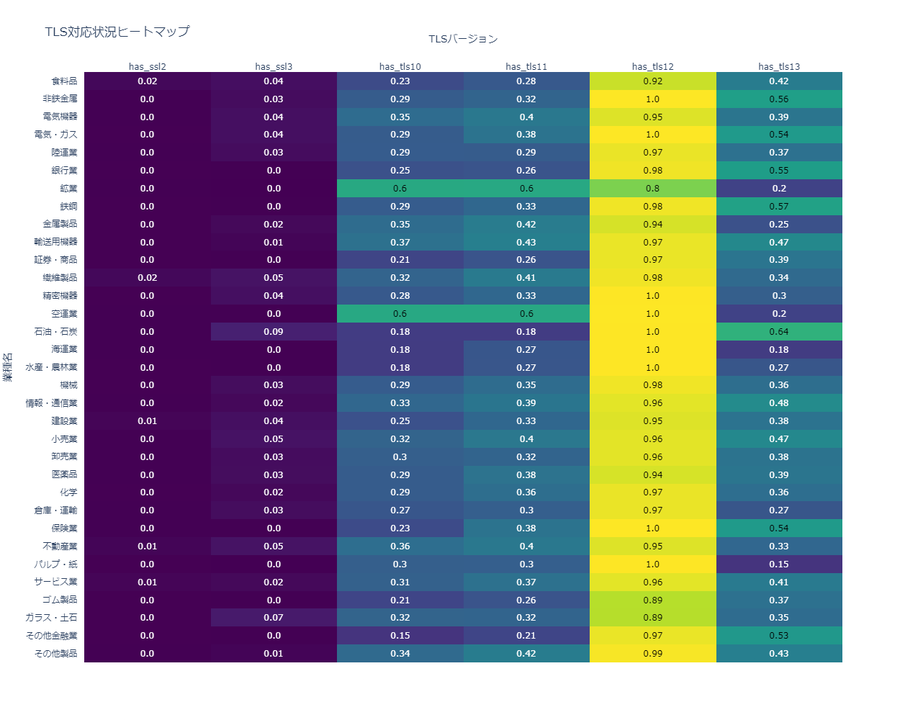
Additionally, the securities industry shows an adoption rate of 39%, banking stands at 55%, and information and telecommunications at 48%. Even in industries handling highly sensitive communications, the adoption rates remain relatively low.

Reasons for Concern
The official websites of listed companies are seen as the "face of Japan's economy" by foreign attackers. For those handling highly confidential or customer-sensitive information, adopting TLS 1.3 is not just advisable but necessary. Even if a website only processes POST requests through contact forms (minimizing exposure), adopting TLS 1.3 is still recommended. The reason is simple: not all users are well-versed in handling sensitive information. Some might, for example, inadvertently input personal data or passwords in plaintext into inquiry forms. Strong encryption, like TLS 1.3, helps mitigate the risks posed by such "human errors." The chain is only as strong as its weakest link, and adopting the latest encryption protocols ensures the highest level of security for safeguarding valuable information assets. This aligns with the duty of care in protecting customer data and serves as part of corporate social responsibility (CSR) — and potentially future compliance obligations — as it all revolves around the protection of customer data.
This is not an exaggeration. Foreign attackers target companies through various attack vectors. In a recent phishing site takedown case handled by our company, the website of a domestic financial institution with a capital of several tens of billions of yen was targeted. Although this was a phishing attack and primarily a social engineering vector, it is not difficult to imagine that technical vulnerabilities may have been profiled during the reconnaissance phase (Recon Phase) of target selection.
[1] The reason for using the websites of listed companies as an example is that when foreign attackers research their targets, they often refer to resources such as investment directories like the "Shikiho," which include URLs of official company websites. Even if sensitive data processing is handled by separate servers, the official website serves as the entry point. This exposes the "weakest link," revealing the lower bounds of a company's security awareness. The cumulative security posture of listed companies' official websites represents the minimum security standard of the Japanese economy as a whole.